Many Organizations Are Vulnerable to Encrypted Attacks, And the Probability Of Being Be a Victim of Such An Attack Is Increasing…
In 2012, we saw a significant rise in the amount of application level attacks and especially encrypted attacks over HTTPS. Many of the online organizations run the majority of their online services over encrypted traffic; services such as Facebook, Twitter, Gmail and many online financial services are available only over HTTPS. Therefore, handling security threats that are carried over encrypted traffic becomes an immediate challenge for almost any company or organization that offers online services.
So, should we be afraid or be concerned? To answer that lets first look at the datacenter network topology and attack threat landscape:
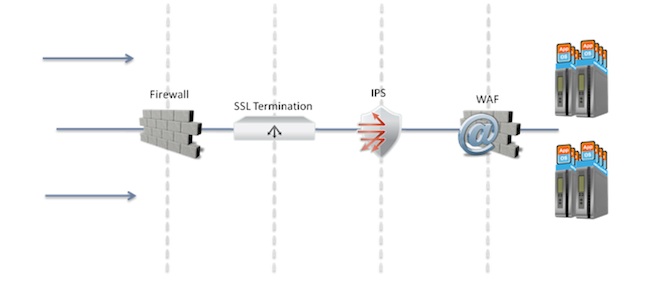
Typically, a datacenter has SSL termination point in front of the cluster servers which is usually an ADC appliance. The reasons to do this include offloading the servers by using dedicated hardware for SSL termination, easier maintenance of SSL software versions and applying of security patches. All security layers that are deployed after the termination point such as IPS, WAF and others allow detecting and blocking many of the attacks. This includes the encrypted ones as the inspected traffic is already non-encrypted.
The layers of defense approach we see above might be the answer for the encrypted attack challenge. However, what will happen if the encrypted traffic includes an availability-based threat vector such as Denial of Service attack or Distributed Denial of Service attack?
In this case, these layers of defense will render pretty useless. The main idea behind encrypted DoS and DDoS attack is that processing of encrypted data consumes more system resources than processing of a non-encrypted data. Thus, encrypted application DoS & DDoS attacks amplify the impact even at relatively low rates of requests per second.
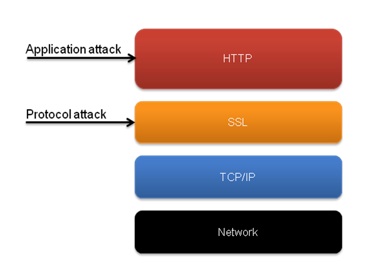
There are two main DoS and DDoS encrypted attack vectors that we see in the wild, each one raises its own challenge:
• SSL protocol level attack
• SSL application level attack
The SSL layer is responsible for producing the cryptographic parameters of the session, which is an operation that typically consumes relatively high CPU resources. The SSL protocol based DoS attacks aim at exploiting known vulnerabilities and design weaknesses in the SSL protocol layer. A typical attack at this layer will try to exploit any known SSL stack vulnerability or to consume the CPU resources by renegotiating the SSL keys over and over again.
The SSL application level DoS or DDoS attack is even more challenging to mitigate. This attack will establish a completely legitimate SSL session and will start to generate a high-rate of web requests from distributed sources such as a botnet. This will eventually place the server in a DoS condition as web requests are at a high-rate and the session is encrypted, amplifying the attack and preventing any new legitimate sessions to be created.
So why is the typical layer of defense approach (shown in figure 1 above) not effective against these threats?
• The encrypted application level flood integrates well with a legitimate form of the application – WAF, IPS and SSL termination offload points devices such as ADC doesn’t include any effective technology that can really differentiate between legitimate to non-legitimate user behavior.
• The centralized SSL termination point will become a “bottle neck” under the stress in which both the protocol-based and application-based encrypted DoS attacks create.
• Firewalls, NG firewalls, WAF and ADC devices are all designed, from bottom-up, to work in a stateful manner. Any stateful device is more vulnerable to application level DoS floods that aim at populating additional states until the application is saturated.
In order to solve this challenge, the network needs to include another layer which is the network wide attack protection. The following diagram illustrates this layer:
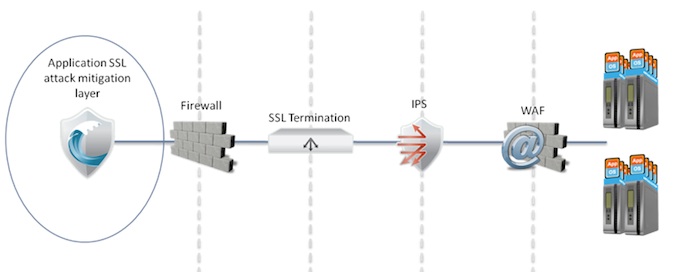
The additional layer at the perimeter and before any stateful device should include the following main capabilities that allow it to identify and resist the encrypted based protocol and application DoS attacks:
1. A dedicated SSL termination engine that allows high performance SSL decryption which will not “break” under massive encrypted DDoS attack.
2. Application behavioral analysis that enable differentiating between legitimate to non legitimate requests even if the protocol and application rules are met.
Summary
Attackers are aware of the increased usage of HTTPS traffic as well as the fact that organizations have not entirely secured their networks against threats that are carried over encrypted traffic. Therefore, attackers take advantage of this blind spot within the organization’s security model in order to launch attacks over HTTPS more than ever before. This means that many of the organizations that offer online services are vulnerable to encrypted attacks and the probability to be a victim of such an attack has significantly increased in the past year. Traditional security solutions cannot detect and mitigate encrypted application DDoS attacks as well as attacks on the SSL protocol layer. Therefore, organizations should look for a solution that can successfully handle these
Share
DEC
2012
