Attackers Exploited Vulnerabilities in ATM Networks Connecting to Bank VPNs and GSM/GPRS Networks, Malware Infected ATMs and POS Systems to Steal Card Data.
A new malware targeting point-of-sale (POS) systems and ATMs has stolen payment card information from several US banks, researchers say. The author behind the malware appears to have links to a Russian cyber-crime gang.

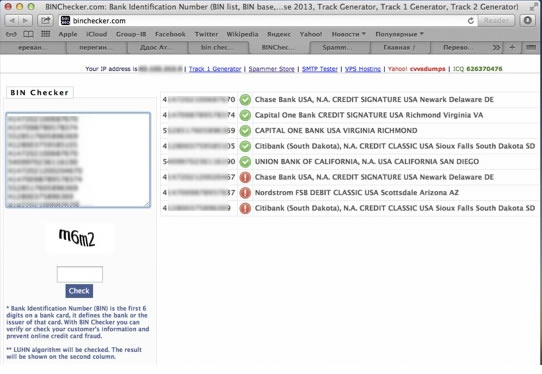
Called “Dump Memory Grabber”, the malware scans the memory of point-of-sale systems and ATMs looking for credit card data, researchers from Russia-based security company Group-IB believe the malware has already been used to steal data from credit and debit cards issued by major US banks, including Chase, Capital One, Citibank, and Union Bank of California.
“We have found one of the C&C servers for the following POS malware, but in fact hundreds of POS/ATMs were infected and we are still investigating this issue,” Andrey Komarov, head of international projects and CTO at CERT-GIB, told SecurityWeek. CERT-GIB is affiliated with Group-IB.
Unlike the more well-known banking malware, which infects individual user computers and intercepts online banking credentials and credit card details, attacks on POS systems and ATMs are far more insidious. In this case, cyber-criminals are infecting ATMs and physical POS systems, such as stand-alone kiosks and modern cash register systems, to harvest information from debit and credit cards.
The Dump Memory Grabber malware collects Track 1 and Track 2 data and transfers the resulting logfile to a remote command-and-control server, according to Group IB. Track 1 and Track 2 refers to data encoded into the magnetic stripe on the physical credit and debit card, and includes information such as the primary account number, first and last name, and expiration date. Criminals can use the information to create cloned physical cards.
Cyber-criminals can use the malware’s administrator panel to switch the transmission type to email, as well. These kinds of attacks are “not surprising,” as it is much easier for cyber-criminals to target dozens of POS systems than to infect tens of thousands of consumer PCs, Aviv Raff, CTO of Seculert told SecurityWeek. “The result at the end is the same,” Raff said.
The newly discovered malware appears to have been written purely in C++ without using any additional libraries, Group-IB researchers said. The malware adds itself to the system registry so that it will automatically run whenever the system boots up. The malware’s payload program lists all the processes running on the system and then searches memory for sensitive data. The malware operator can limit the search to the memory of a specific application process or scan across all applications, according to Group-IB.
The output.txt log containing the memory dumps and stolen credit card data are transferred to a remote server via FTP. The IP address of the remote server is assigned to a network operated by Selectel, a Russian Internet Service Provider based in Moscow. It is also associated with a domain name belonging to a Russian company named “CISLAB” and was registered back in 2010.
Clues in the video suggest the malware author is from the Russian Federation and goes by “Wagner Richard” on Russian social networking site Vkontakte, Group-IB said. It appears “Wagner Richard” also accepts orders for distributed-denial-of-service attacks.
This person is likely involved with a “big cyber-crime gang,” and is probably acting as an administrator for the group, Group-IB concluded. The group appears fairly active with DDoS attacks, offering its services for just $2 an hour and private DDoS bots for $800. The group claims to be able to bypass anti-DDoS services offered by Qrator, Cloudflare, and Cisco Guard, Group IB said.
Group IB researchers believe several of the cyber-crime gang members are active in a Russian-offshoot of the Anonymous collective, and include individuals from Ukraine, Armenia, and Moscow. Most of the members appear to be less than 23 years old.
Most of the POS/ATM attacks Group-IB analyzed relied on the “help of insiders,” such as the employees in charge of maintaining POS systems and authorized to update the software, the security firm said. A few POS systems running Windows XP or Windows Embedded with Remote Desktop or VNC software were infected remotely, and in some cases, attackers exploited vulnerabilities in ATM networks connecting to the bank’s VPN or GSM/GPRS networks, according to Group IB.

Dump Memory Grabber is not the first malware family to target POS and ATMs. Seculert has observed different malware families targeting POS systems recently, Raff said. A few months ago, the company warned about Dexter, which infected POS systems at well-known retail outlets, hotels, and food establishments and captured card data during the sales process. Dexter is believed to have stolen nearly 80,000 credit card records at several Subway restaurants last year. Infection vectors include physically inserting a malicious USB drive, or via the Web if the target system was directly connected to the Internet.
Seculert at the time estimated 42 percent of Dexter infections were in North America, and researchers have seen several new Dexter variants since then, Raff said.
McAfee security researcher Chintan Shah also identified vSkimmer, a Dexter successor, just last week. Shah claimed vSkimmer has more functionality compared to Dexter, and can capture credit card data from Windows systems running payment processing software. The vSkimmer malware can either transfer the stolen information over the Web to a remote server, or download the data onto a USB drive. “VSkimmer is another example of how financial fraud is actively evolving,” Shah wrote in the post.
Boston-based retailer Blanchard’s Liquors notified customers Monday that it had found malware on its POS systems over the weekend and some customers had been hit with fraudulent charges. The company immediately took down its credit card terminals and believes “the issue was contained by Saturday,” according to the statement. It’s not known at this time which malware was responsible, and the investigation is still ongoing.
Group-IB said it has shared its findings on “Dump Memory Grabber” with Visa, the affected banks and US law enforcement agencies.
ShareAPR
2013
