The Cutwail botnet, which has already been spreading the banking trojan known as Zeus, is now also trying to pass around a new Android trojan called Stels. Stels infects Android devices by pretending to be an update for Adobe Flash Player. In case potential victims aren’t on an Android device, the developers of the malware have come up with a backup plan – if the dangerous spam links are opened in a browser, such as Internet Explorer, on a desktop or laptop computer, users are redirected to web pages where the Blackhole exploit kit lies in wait. A security team at Dell has published a more detailed analysis of the attack scenario.
According to the analysis, the attacks start with spam emails claiming to be from the Internal Revenue Service, the tax agency in the US. If a user clicks on the link in the email, a script investigates whether an Android device is being used. If not, and if the victim is using Internet Explorer, Mozilla’s Firefox or Opera, they are redirected to a web page serving as a façade for the Blackhole exploit kit, which then tries to exploit out-of-date browser plugins in an attempt to infect the computer.
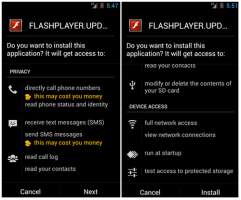
If, however, the script does actually discover that it is on an Android device, it sends the user to a web page offering a Flash Player update. In order to install the fake update, the user must have “Allow apps from unknown sources” enabled.
Once the update is approved, the trojan is installed – and when the supposed app is opened for the first time, it announces that the update did not work and will be uninstalled. Of course, Stels continues to run in the background, setting up a backdoor to download more malware. The trojan can also spy on the victim’s contact list, send text messages that cost money, make telephone calls and filter text messages to look for, say, mTANs. Working with a Zeus trojan, Stels could thus potentially get around two-factor authentication.
However, the trojan does not dig very deep into the Android operating system – it does not use root access or try particularly hard to hide itself. The supposed Flash update can therefore easily be found among the “active apps” in the settings menu and uninstalled. Before the “app” is launched for the first time, its name should also raise some suspicions, with “Appname” briefly appearing under the icon.
ShareAPR
2013

